I don’t even know where to start my questions ![]()
Let me preface this long thread by saying that I have read Self-managed Grist - Grist Help Center and most related pages and am still struggling to understand the whole concept related to teams, organizations, users and authentication. I’d appreciate any clarifications even simple links to documentation I might have missed.
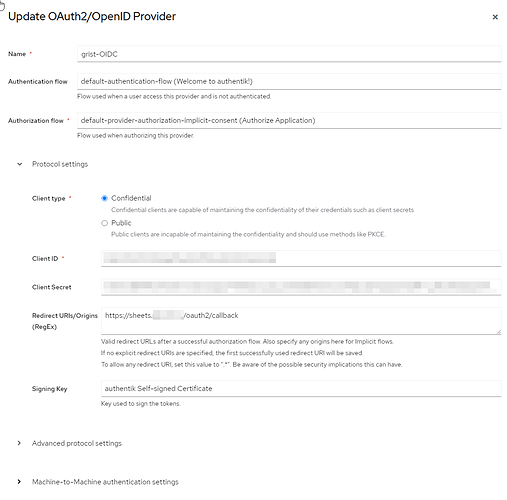
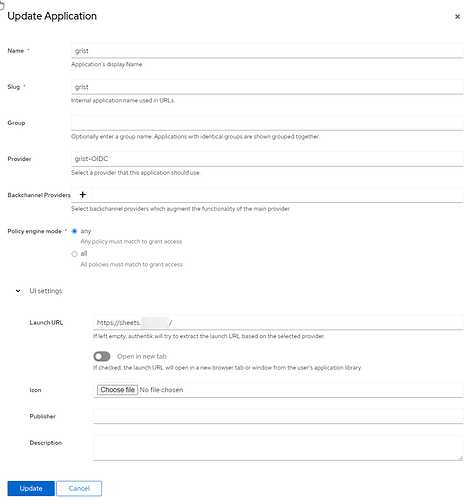
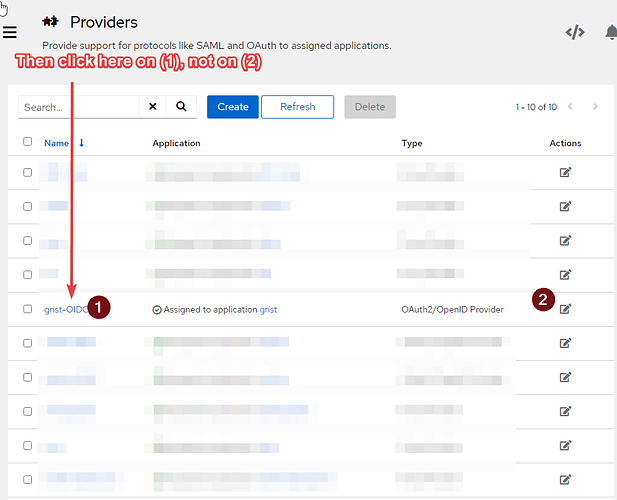
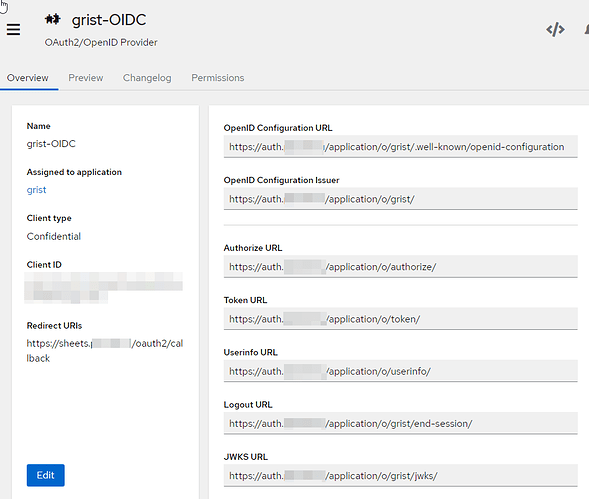
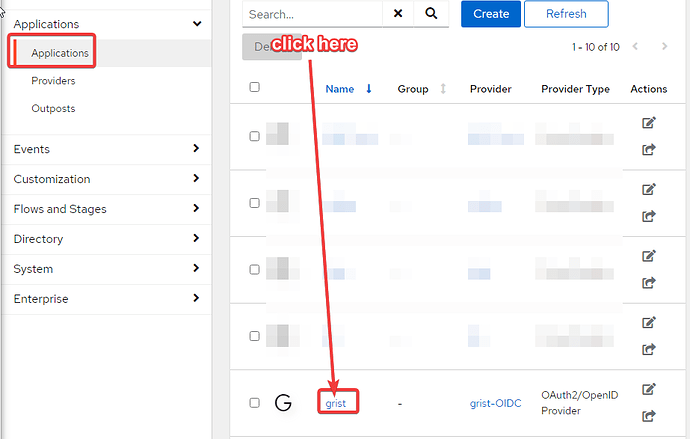
if anyone is using authentik + OIDC I’d be very happy to compare the settings in authentik. I had to guess at most of them.
My first try at a self-hosted grist instance was using authentik as a reverse proxy authentication. This worked perfectly fine. I also added these envs to my compose file:
- GRIST_DEFAULT_EMAIL=me@domain.tld
- GRIST_SINGLE_ORG=sheets
This way, as soon as I logged in via authentik, I was logged in into grist, with this single email address and had access to the admin panel and the team called “sheets”
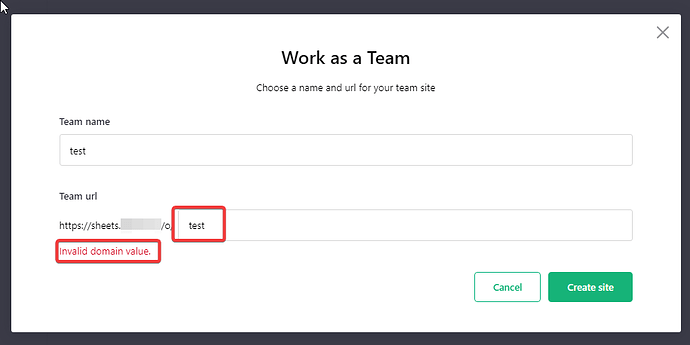
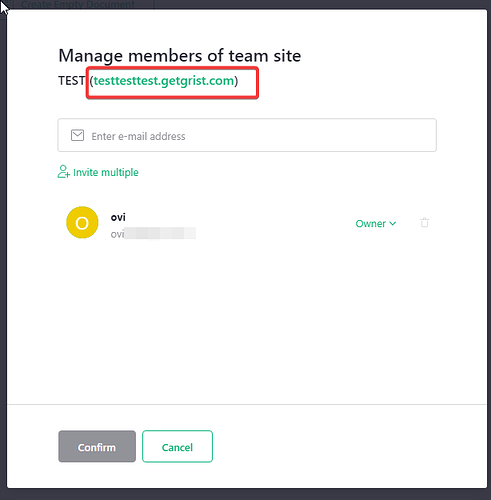
My next try was to use authentik as an OIDC provider and then I also experimented by enabling multiple team sites.
This meant removing these two envs:
- GRIST_DEFAULT_EMAIL=me@mydomain.tld
- GRIST_SINGLE_ORG=sheets
And adding these:
- GRIST_OIDC_IDP_ISSUER=https://authentik.mydomain.tld/application/o/grist/.well-known/openid-configuration
- GRIST_OIDC_IDP_CLIENT_ID=secretXXX
- GRIST_OIDC_IDP_CLIENT_SECRET=secretXXX
- GRIST_ORG_IN_PATH=true
This also worked in the sense that I could log into grist when logged into authentik. Since my authentik suer uses the same email as I used for GRIST_DEFAULT_EMAIL this worked just fine.
Now here are the confusing parts:
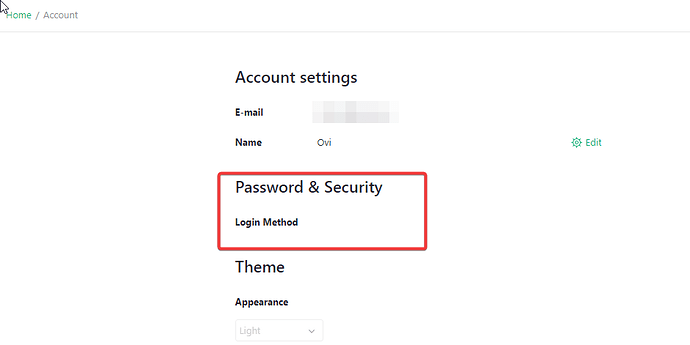
The login method does not reflect in my grist user profile:
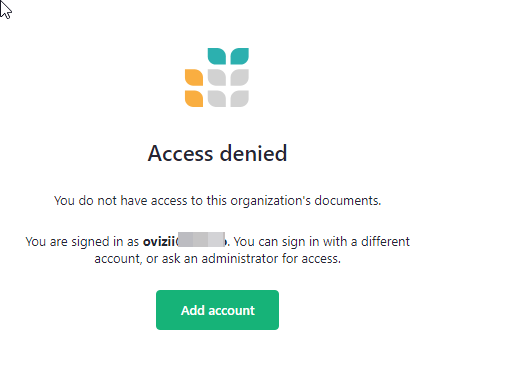
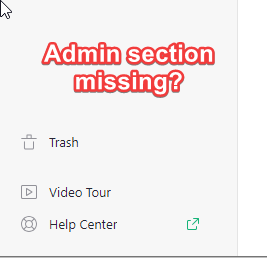
I am now missing any link to the grist admin panel:
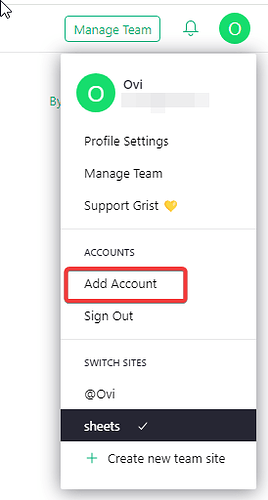
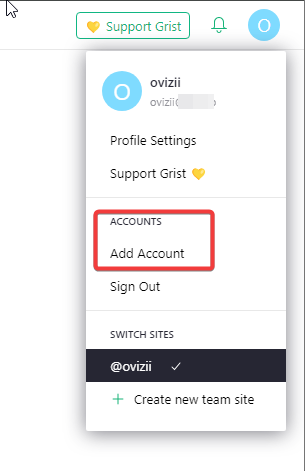
A new option to “add account” has appeared. To what/where do I add these accounts? To grist? To my team? This will not work anyway, since I guess it needs to be properly set up and redirected to some authentik signup page, which I haven’t done. Just asking for clarity’s sake.
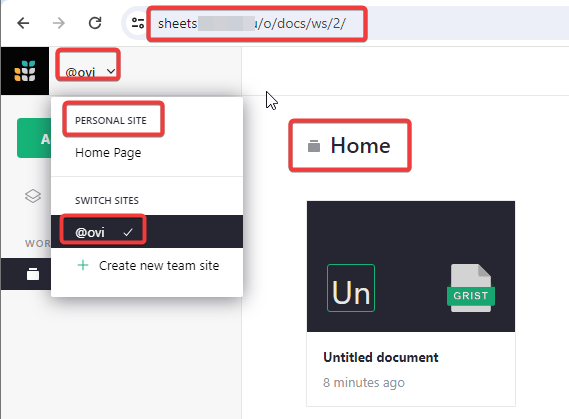
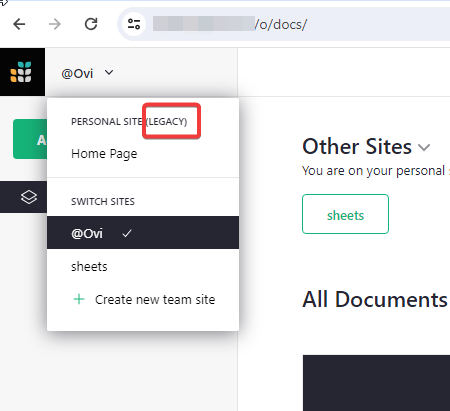
Why does it say “legacy” next to the personal site? All I find about personal sites is this: Creating team sites - Grist Help Center - waht are they? Are they meant for sheets not shared with a team?
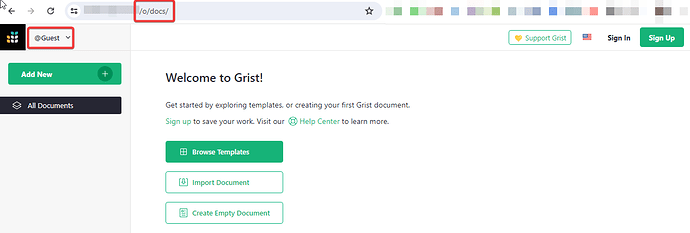
I just wanted to mention, that after signing out of both grist and authentik, and randomly clicking back and forth I somehow ended up on my grist instance as a guest. I didn’t even know this was possible, not sure how to get back here on purpose except for manually typing in the URL, but I am wondering what I can do as a guest? It looks like anyone can get here as a guest and add new docs?